ABSTRACT
The significance of correct identification of plants is acknowledged in many human endeavours such as health care, food production, sustainable housing, forest resources management and environmental protection. Plant identification is usually carried out by means of descriptions and keys, which are available in floras, manuals or other taxonomic publications, the most widely used tool being the dichotomous key. However, the construction and navigation of dichotomous keys are tedious. Thus identification is viewed by many practitioners as onerous task, which has led to declining interest in plant taxonomy. Therefore, the objective of this paper is to simplify the writing and application of the dichotomous key format, with the aim of making the practice of plant taxonomy more attractive, less laborious and dreaded for upcoming students of biology. A proposal on step-by-step, readily comprehensible procedure for making a dichotomous key from a conventional table of character comparison is presented. Some basic features of the key format (that is, couplets, leads, references, pointers, and endpoints), its variants (that is, indented and bracketed), and applicable enhancements, such as looping, nesting, and reticulations, use of polychotomous leads and tabula are illustrated and discussed.
Key words: Bracketed key, computerised key, diagnostic key, indented key, identity confirmation, nested key, reticulation, taxonomic key.
Identification is one of the major activities in plant taxonomy, and usually involves the use of descriptions and keys, which are available in floras, manuals or other taxonomic publications such as Hutchinson and Dalziel (1963-1972), Keay et al. (1964), Lowe and Stanfield (1974) and Keay (1989). The necessity for correct identification of plants is acknowledged across all human endeavours, from health care (Upton and Romm, 2010), food production, sustainable housing, criminal justice and forest resources management to environmental protection (Bock and Norris, 2015). In health care delivery, medicinal plants misidentification and misrepresentation are well known root causes of herb adulteration or substitution, which in turn can cause serious health problems to herbal drug consumers (Panter et al., 2014), and ignite bad publicity and legal burdens for the pharmaceutical industry (Dukes, 2005).
Pankhurst (1991) recalled that taxonomic keys, albeit unpublished, had been used for several hundreds of years. Identification keys were also said to have been presented by Richard Waller in 1689 to his assembled colleagues at a meeting of the Royal Society in the form of image-based dichotomous keys for the herbs of Britain (Griffing, 2011). Evidence from the literature points to the possibility that the dichotomous key format, which consists of exactly two choices at each branching point, was a form in which taxonomic keys were first published in 1672 and 1778 (Griffing, 2011). Dichotomous key is one of the single-access devices for identification in which the sequence and structure of identification steps are fixed by the author of the key. In all single-access keys, there is only one point of entry; and so, as much as possible, such keys are made to start with characters that are reliable, convenient and generally available throughout most of the year. In reality, these conditions are not often achievable for all the taxa in a key. A random-access or multiple-access, key is an identification tool that helps to overcome this challenge by letting the user make character choices in the key according to the state of the plant specimen being identified, and the prevailing circumstances such as seasonal variations, and field situations (Bock and Norris, 2015).
The dichotomous key is widely acknowledged as the most popular type of identification tool (Tofilski, 2018), and had been a clever means of organising taxonomic information before the age of computers (Godfray et al., 2007). The use of this key format is known to have contributed to increasing the quality and durability of knowledge of plant classification acquired in comparison to traditional teaching techniques (Andic et al., 2019). It is also an established method for teaching plant identification skills to learners (Stagg and Donkin, 2013). However, opinions from many quarters point at construction and navigation of dichotomous keys as daunting tasks for many students (Jacquemart et al., 2016). Due to these challenges, there is declining interest in the practice of plant identification. Therefore, this paper aimed at simplifying the construction, and elucidating the principal features, and functionality attributes of dichotomous key format, with the purpose of making the practice of plant taxonomy more attractive, less laborious and dreaded.
Data procurement for purpose of illustration
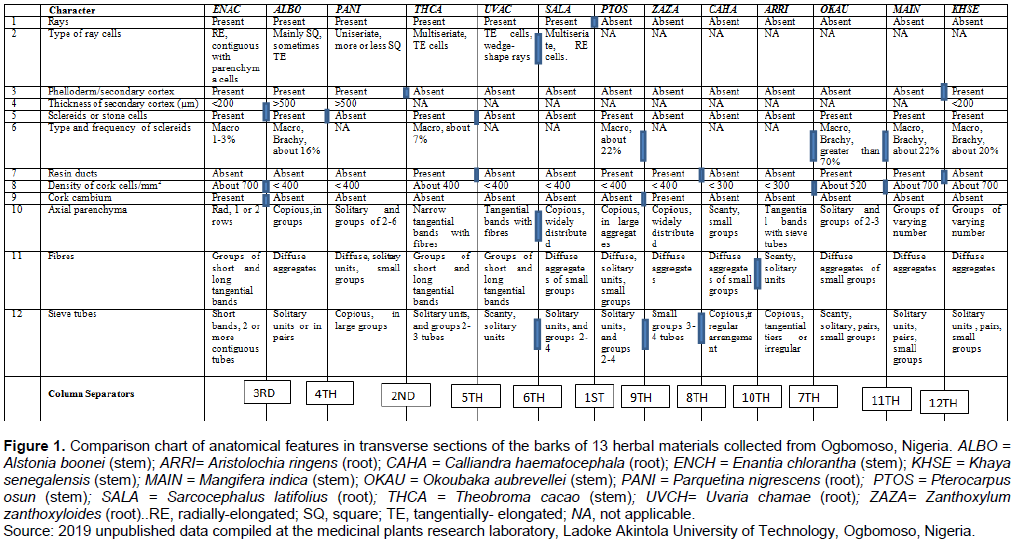
Anatomical data on the barks of 13 medicinal herbs (Figure 1) marketed as roots, root barks and stem barks in Ogbomoso township in Nigeria were sourced for the purpose of illustration from the 2019 compilation of unpublished results at the medicinal plants research laboratory in the Department of Pure and Applied Biology, Ladoke Akintola University of Technology, Ogbomoso, Nigeria. The data items were taken in accordance with the standard procedures: tissue sectioning/maceration (Lin et al., 1995), staining (Mota et al., 2017), mounting and microscopic observations (Miranda et al., 2018), while the terminology and descriptions of observed features followed those of the International Association of Wood Anatomists (IAWA Committee, 1989). Fourteen characters, consisting of nine qualitative and five quantitative features, all of which were diagnostic of the species were compiled and used to build the conventional table of character comparison (Figure 1). Only transverse sections and tissue macerations of the barks were studied. Staining was done in 1% alcoholic safranin, mounting was carried out in Canada balsam and observations made using an Olympus binocular biological microscope (CH20i Model). Quantitative characters were considered diagnostic of the species only if the means of the replicated values were statistically significant at α = 5 following One-Way Analysis of Variance, and Duncan multiple range classification of the means (Landau and Everitt, 2004).
Conceptualisation of a procedure for construction of dichotomous key
The procedure for writing out a dichotomous key with relative ease for a given number of taxa based on certain observable features was heuristically conceptualised as a recursive/repetitive process of ‘divide and conquer’ algorithm (Hagedorn et al., 2010), which was systematically executed in this study, and is being proposed as a number of logical steps:
Step I: Build and use as the starting point, a table of character comparison (Figure 1), with which most researchers in systematic biology are familiar;
Step II: Using the primary or first level of column separator(s) in form of stickers, the table of character comparison is partitioned into two blocks based on the characters shared by the columns;
Step III: Each of the two main blocks is further partitioned using the second, third, fourth, etc., levels of stickers until the table has been resolved into the individual columns or species by the stickers;
Step IV: A pair of contrasting statements or ‘leads’ are constructed as a ‘couplet’ from each of the characters or character combination at each level of separator; thus in this case with 13 taxa (columns) and 12 characters/character combinations (rows), the outcomes of steps II to IV translate into further steps as follows:
Step V: Using the first level column separator(s) indicated in character number 1, the comparison chart (Figure 1) was partitioned into two mutually exclusive main blocks of six columns on the left block and seven columns on the right;
Step VI: Considering first, the left-hand side main block of six columns obtained in step V above, a second level column separator/sticker shown in character number 3 was used to further partition the block into two mutually-exclusive smaller blocks of three columns each;
Step VII: Again considering first, the three left-hand side columns obtained at the end of step VI, three 3rd level column separators (indicated in character numbers 4, 8 and 9) were used to fragment the block to produce one column (that is, Enantia chlorantha) on the left, and two columns (that is, Alstonia boonei and Parquetina nigrescens) on the right, each being mutually-exclusive;
Step VIII: A fourth level column separator, indicated in character number 5 was used to separate the two right hand side columns of A. boonei and P. nigrescens that resulted from the end of Step VII;
Step IX: Now considering the second three columns produced by the second level sticker (or character number 3) in step VI, two 5th level column separators indicated in character numbers 5 and 7 were used to resolve the block into one column (Theobroma cacao) on the left and two columns (Uvaria chamae and Sarcocephalus latifolius) on the right;
Step X: Using three 6th level column separators in character numbers 2, 10 and 12, the two right hand side columns of U. chamae and S. latifolius obtained at the end of step IX were separated, thereby bringing into completion the resolution of all the six taxa in the left hand side main block of step V into the individual species;
Step XI: Finally, considering the right-hand side main block of seven columns obtained in “Step V”, and following similar procedures in steps VI to X , the indicated number of seventh, eighth, ninth, tenth, eleventh and twelve level column separators were used to resolve the seven taxa into the individual species;
Step XII: From each level of the column separators 1st, 2nd, 3rd,….to 12th, all the respective diagnostic characters or character combinations were used in turn to construct a pair of contrasting statements: 1a and b from the 1st; 2a and b from the 2nd; 3a and b from the 3rd…12a and b from the 12th. The statements were presented hierarchically in form of loops in a way that statement number 1a connects to number 2a and b; 2a flows into 3a and b; 3a into 4a and b; 2b into 5a and b; and 5a into 6a and b, thereby obtaining a nested system of loops within the generic loop created by statement number 1a. Similarly, statement number 1b connects to number 7; 7 flows into 8; 8 into 9, etc., up to, and ending in, statements number 12a and b to obtain a non-reticulated dichotomous key as shown in Figure 3. As done in this study, it is recommended that the entry-controlled type of statements in the form of ‘For…. Loop’ or ‘While… loop’ (Guru99, 2020) should be adopted because it is more appropriate to the mode of stating ‘couplets’ which provides that the condition in a statement be satisfied first, before the next statement can follow;
Step XIII: As an alternative to ‘step V’ (if so desired), or if it is impracticable to partition the table of character comparison (Figure 1) into two mutually exclusive blocks, then, the table is fractionalised into two non-mutually exclusive sub-tables (that is, which allow overlap of column characteristics), each displaying a portion of the parent table. If so desired or necessary, each of the sub-tables is independently further fractionalised in like manner to obtain two new sub-tables; this exercise of generating two sub-tables from one, resulting in a nexus of tables within a table may continue until the columns of taxa in the innermost/most recent sub-table in each case are successively separable by means of stickers into mutually exclusive blocks as earlier described (Figure 2);
Step XIV: Considering the outermost or the first two sub-tables in a similar way as the first level of column separator in step XII, progressing systematically to the second, third, etc., up to the innermost sub-table and eventually to the mutually exclusive blocks/columns in each case, repeat step XII using Figure 2 to obtain pairs of contrasting statements that constitute another dichotomous key (with reticulation).
Thus, Figure 2, which contains two non-mutually exclusive sub-tables from a table of character comparisons, was considered for construction of another variant of dichotomous key (that is, with reticulation). Generation of sub-tables was carried out only once for the sake of simplicity, while the stickers/column separators indicated in Figure 2 were considered for generation of paired contrasting statements as explained in Step XII.
Structure of the dichotomous key
The two dichotomous keys obtained from this study (Figures 3 and 4) are the products, respectively generated at the end of steps XII and XIV of the proposed procedure. While Figure 3 is a non-reticulated key, Figure 4 is enhanced with reticulations. Each of the two keys in Figures 3 and 4 is of dichotomous format, and as it is characteristic of all dichotomous keys, each couplet in the keys can be seen to consist of two contrasting sets of statements or ‘leads’, otherwise called assignment statements; and at the end of each ‘lead’ is a reference, which is either a number pointing to another couplet, or a text indicating the name of a taxon. Tofilski (2018) referred to these references as “pointer” and “endpoint”, respectively. Identification using a dichotomous key starts at couplet one and it is stepwise. At each step, the user reads both ‘leads’ of a ‘couplet’ and chooses one that better fits the specimen for identification. If the chosen ‘lead’ is associated with a ‘pointer’, then the user goes to another ‘couplet’, which is the next step of the exercise. Identification has been accomplished when a chosen ‘lead’ is associated with an ‘endpoint’.
Variants of the dichotomous key
On the basis of arrangement of couplets, Saupe (2009) classified printable dichotomous keys into two, namely: indented or yoked, and bracketed or linked types. In an indented key (Figures 3 and 4), each successive couplet is indented with an equal distance from the left margin and the indentation increases with increasing number of couplets. Additionally, the couplets are looped, and the loops nested in a way that two or more lower-level (or recent) couplets are subsumed under a higher-level (or earlier) assignment statement of couplet. This variant of dichotomous key is therefore also termed nested. In the bracketed key, both choices in a couplet are listed contiguously, that is, they are placed next to each other, starting from the same point at the left margin. Saupe (2009) enumerates three advantages of indented keys: similar taxa are grouped together; user can rarely get lost in navigating a key; they are faster or more efficient to use than bracketed type; and it is easier to retrace one’s steps in case a wrong choice has been made. Although nested keys are more commonly known as “indented”, it is important to understand that indentation refers to an accidental (albeit frequent) rather than essential quality of the key format. This, according to Pankhurst (1991), is because nested keys may be printed without indentation to preserve space (relying solely on corresponding lead symbols) and linked keys may be indented to enhance the visibility of the couplet structure.
In each of the two main loops in the key shown in Figure 3, it can be observed that the assignment statements which respectively terminate the loops, namely: 6a and b on one hand and 12a and b on the other hand, are not found in the innermost loop in each case. If they had been so, two perfect nested loops would have been achieved. Instead, there are ‘odd statements’, that is, those lying outside their innermost loops, e.g. statements number 3b, 4a and b, and 5b. Similar observations can be made in Figure 4 regarding statements number 7a and b on one hand, and 15a and b on the other hand. The two keys from this study are therefore illustrative of imperfect nested looping statements (Yin et al., 2016), a condition frequently observed in indented (or nested) dichotomous keys. It is however possible to observe one or more perfect nested loops lying within an imperfect main loop as in loops 2a and b in each of which the respective terminal statements 4a and b, and 6a and b are the innermost loops.
Imperfect nested looping of more intricate connection often occurs in long keys, in which one or more of a set of loops at a given hierarchical nesting level may connect with or flow into a couplet outside of its nesting level. For example, an assignment or reference statement under the main loop 1a may point at, or direct a user to a statement under a main loop formed by 1b. This condition, though not illustrated here, is possible and practicable. Such connectivity negates the provision of looping in its strict sense, and is attributable to complexity in the nature of plants, with possible extensive overlaps of features observable in the taxa making up a group (Kirchoff, 2001). Generally speaking, the subject matter of nesting and connectivity between the different parts of a key paves the way for a clear understanding of the concept of reticulations in single access keys.
Reticulation in dichotomous keys
While introducing the concept of reticulation in writing of dichotomous keys, Osborne (1963) argued out the possibility to arrange the couplets in a key, such that even a wrongly answered question can lead to correct identification, provided that most of the questions in the relevant couplets are answered correctly. Reticulation connects different branches of the identification tree so that in a reticulated key, multiple paths lead to the same result, and thus, the data structure changes from a simple tree to a directed acyclic graph (Fantom Foundation, 2018). A reticulated key usually increases the probability of correct identification for those taxa specifically affected by the reticulation; this means that reticulation improves the usability of a key. However, addition of reticulation often diminishes the overall probability of correct identification averaged over all the taxa involved (Osborne, 1963). Two forms of reticulation have been identified namely, terminal and inner reticulations (Payne and Preece, 1977). In terminal reticulation, a single taxon (or next- level-key as the case may be) is keyed out in two or more locations in a key (Figure 4), while in an inner reticulation, a couplet with further leads can be reached through more than one path (See for example, the keys to the Nigerian trees of Groups A to I by Keay (1989)).
Other means of enhancing functionality of the dichotomous key
The admonition credited to Confucious: “If a craftsman wants to do good work, he must first sharpen his tools”, is also useful in taxonomy. Being the taxonomists’ most frequently used tool for plant identification, no amount of efforts committed to enhancing the features and functionality of dichotomous key should be viewed as excessive. So for all practical purposes, it will not be out of place to build in a wide margin of flexibility at the time of writing a key. In addition to employing looping, nesting and reticulation, other practicable means to enhance the functionality of dichotomous key include introduction of three or more choices (or polychotomous leads) at appropriate levels and branching points in line with observed variations in the features of the taxa involved (Strain and Chmielewski, 2010), and use of tabula; that is, illustrations or representations in the form of drawings, photographs or herbarium, live specimens or even video clips. Introduction of more than two choices at strategic branching points effectively reduces the number of couplets, so the key is shorter and there is the possibility of carrying out identification with minimal stress and error (Strain and Chmielewski, 2010). On the other hand, insertion of illustrations in form of diagrams, etc., may disproportionately lengthen a key, but either of the two enhancement approaches has its advantages. With such enhancements, however, the tool in the strict sense should better be re-named as identification, diagnostic or pictorial key as the case may be (National Center for Environmental Health, 2013).
Weaknesses of the dichotomous key
It follows from the forgoing account that there is only one point of entry into a dichotomous key, so that there is a single path to be followed by the user. This is a property shared by all single-access key formats. A disadvantage of this arrangement is the problem of ‘unanswerable couplet’; that is, a user may get stuck and identification will be impossible if a choice cannot be decided at any point (Hagedorn et al., 2010). Also of concern are the issues of ‘dead ends’, and the ‘momentary distractions’ that can cause a user to forget his or her position in a key (Walter and Winterton, 2007). These situations can arise when a character cannot be observed or adequately scored (e.g., when the feature is in its developmental stage or is season-based, and hence not visible in the specimen) or because the options are not stated clearly enough in the key. The magnitude of the frustration that may set in due to these problems can be intolerable, especially by novice taxonomy students. Circumventing these challenges hinges upon the author’s expertise in choosing characters that are reliable, cost-effective, readily observable across all the taxa involved, and available throughout most part of the developmental cycle of the plants (Hagedorn et al., 2010). The problem of ‘unanswerable couplet’ is surmountable by making use of random-access keys instead.
Confirmation of plant identity, rather than identification in the strict sense, is what a taxonomist sometimes desires, especially if a particular name has been suspected of a specimen. One expects an ideal tool for identification to be equally usable for identity confirmation, and one might question the functionality of a tool if it cannot assist in such a circumstance. A scrutiny of Figures 3 and 4 will reveal that these keys are not applicable for confirming the identities of the constituent species without having to pass through the regular identification process. This is another major weakness of the paper-based dichotomous keys.
Automation of construction and navigation of identification keys is also most desired nowadays, but the format and style of a key are important features that determine if it can be so automated by computerisation (Iacono and Kling, 1996). A key, which on account of its design or format allows objective comparison of large amount of data and rapid information processing by electronic means, is referred to as being programmable. In truth, one notable challenge in the application of paper-based dichotomous keys is that of being hardly, if at all, programmable; and this is predicated upon their design. Among the foremost efforts to electronically tackle the issue of automation of dichotomous keys were those of Pankhurst (1970) and Payne (1981, 1988) whose outcomes did not seem to enjoy much acceptivity. Recently, Tofilski (2018) came up with “Dkey”, a software to alleviate the problem associated with construction and use of dichotomous keys. With the software, various editing options have been made possible, including moving, rewriting and re-numbering of couplets as well as combining keys and generating edited keys in the traditional text format for printing. Regarding the second aspect of the problem, Dkey makes ‘pointers’ clickable in order to move from couplet to couplet, thus making identification faster and easier. Another notable contribution towards enhancing the performance of single access keys was the development of an index by Sinh et al. (2017) to quantitatively evaluate dichotomous keys. Despite all these efforts, computerisation of nested dichotomous keys with inner reticulations is still believed to be associated with some challenges (Yin et al., 2016).
CONCLUSIONS AND RECOMMENDATIONS
Based on the expositions from this study, one might argue that although dichotomous key is inevitable as a tool for teaching taxonomy and routine identification exercises, it seems that its weaknesses demoralisingly outweigh its strengths. Contrary to these opinions however, and without prejudice to the arguments thus far, it can be concluded that the mystery behind the acts of writing and using dichotomous keys has been solved; the salient features and functionality attributes of the key format have been elucidated; the prospect of enhanced practice of plant identification is achievable; and increased interest in taxonomy by upcoming students of biology can be assured; only, the identified areas of weakness of dichotomous key format should be addressed for better performance, while considerations should be given to creation of new key formats with improved functionality.
The author has not declared any conflict of interests.
The author thanks Mrs. Jennifer Ideh and Mr. Gideon Olaniran at Medicinal Plants Research Laboratory, Ladoke Akintola University of Technology, Ogbomoso, Nigeria for assisting to collate the wood-bark anatomical data of some medicinal herbs used for illustration.
REFERENCES
|
Andic B, Cvijeticanin S, Maricic M, Stesevic D (2019). The contribution of dichotomous keys to the quality of biological knowledge of eighth grade students. Journal of Biological Education 53(3):310-326.
Crossref
|
|
|
|
Bock JH, Norris DO (2015). Forensic plant science. Academic Press.
Crossref
|
|
|
|
|
Dukes MNG (2005). The law and ethics of the pharmaceutical industry. Elsevier.
Crossref
|
|
|
|
|
Fantom Foundation (2018). An introduction to directed acyclic graphs and how they differ from Blockchains. Available at:
View
|
|
|
|
|
Godfray HCJ, Clark BR, Kitching IJ, Mayo SJ, Scoble MJ (2007). The web and the structure of taxonomy. Systematic Biology 56(6):943-955.
Crossref
|
|
|
|
|
Griffing LR (2011). Who invented the dichotomous key? Richard Waller's watercolours of the herbs of Britain. American Journal of Botany 98(12):1911-1923.
Crossref
|
|
|
|
|
Guru99 (2020). C Loops: For, While, Do While, Looping Statements with Example. Available at:
View
|
|
|
|
|
Hagedorn G, Rambold G, Martellos S (2010). Types of identification keys. In: tools for identifying biodiversity; progress and problems, Nimis PL, Vignes LR (eds.), EUT pp. 59-64.
|
|
|
|
|
Hutchinson J, Dalziel JM (1963-1972). Flora of west tropical Africa; Vol. I, II, III; Crown for oversea governments and Administration, London.
|
|
|
|
|
Iacono S, Kling R (1996). Computerization movements and tales of technological utopianism. In: Computerization and controversy 2nd Edition, Kling R.(ed.), Academic Press, Inc. pp. 85-105.
Crossref
|
|
|
|
|
IAWA Committee (1989). International Association of Wood Anatomists (IAWA) list of microscopic features for hardwood identification. IAWA Bulletin, New series 10(3):219-332.
Crossref
|
|
|
|
|
Jacquemart AL, Lhoir P, Binard F, Descamps C (2016). An interactive multimedia dichotomous key for teaching plant identification. Journal of Biological Education 50(4):442-451.
Crossref
|
|
|
|
|
Keay RWJ (1989). Trees of Nigeria. Clarendon Press, Oxford. P 476.
|
|
|
|
|
Keay RWJ, Onochie CFA, Stanfield DP (1964). Nigerian trees Vol. II Nigerian National Press, Lagos.
|
|
|
|
|
Kirchoff BS (2001). Character description in phylogenetic analysis: insights from Agnes Arber's concept of the plant. Annals of Botany 88:1203-1214.
Crossref
|
|
|
|
|
Landau S, Everitt BS (2004). A handbook of statistical analyses using SPSS, Chapman And Hall/CRC Press Company, Washington, D. C. Available at:
View
|
|
|
|
|
Lin JX, Hu YX, Wang FH (1995). Wood and bark anatomy of Nothotsuga (Pinaceae). Annals of the Missouri Botanical Garden 82(4):603-609.
Crossref
|
|
|
|
|
Lowe J, Stanfield DP (1974). The flora of Nigeria. Sedges (Family Cyperaceae), Ibadan University Press, Ibadan.
|
|
|
|
|
Miranda AD, Palhares D, Cury NF, Pereira LAR, Silveira CEDS (2018). Comparative wood and bark anatomy of stem, root and xylopodium of Jacaranda ulei (Bignoniaceae). Balduinia 64:1-18.
Crossref
|
|
|
|
|
Mota GS, Sartori CJ, Miranda I, Quilhó T, Mori FA, Pereira H (2017). Bark anatomy, chemical composition and ethanol-water extract composition of Anadenanthera peregrina and Anadenanthera colubrine. PLoS ONE 12(12):e0189263.
Crossref
|
|
|
|
|
National Center for Environmental Health (2013). Pictorial keys to Arthropods, Reptiles, Birds and Mammals of Public Health Significance. Centers For Disease Control and Prevention (CDC),US Department of Health and Human Services. Available at:
View
|
|
|
|
|
Osborne DV (1963). Some aspects of the theory of dichotomous keys. New Phytologist 62(2):144-160.
Crossref
|
|
|
|
|
Pankhurst RJ (1970). A computer program for generating diagnostic keys. The Computer Journal 13(2):145-151.
Crossref
|
|
|
|
|
Pankhurst RJ (1991). Practical taxonomic computing. Cambridge University Press, Cambridge, UK.
|
|
|
|
|
Panter KE, Welch KD, Gardner DR (2014). Poisonous plants: biomarkers for diagnosis. In: Biomarkers in Toxicology, Gupta RC (ed.), Elsevier, Oxford, UK. pp. 563-589.
Crossref
|
|
|
|
|
Payne RW (1981). Selection criteria for the construction of efficient diagnostic keys. Journal of Statistical Planning and Inference 5(1):27-36.
Crossref
|
|
|
|
|
Payne RW (1988). Identification keys, diagnostic tables and expert systems. In: Edwards D, Raun NE (eds.), Compstat, Physica-Verlag Heidelberg. Available at:
Crossref
|
|
|
|
|
Payne RW, Preece DA (1977). Incorporating checks against observer error into identification keys. New Phytologist 79:203-209.
Crossref
|
|
|
|
|
Saupe SG (2009). Plant identification: featuring taxonomic keys. College of St. Benedict/St. John's University, Collegeville, MN56321.
|
|
|
|
|
Sinh NV, Wiemers M, Seettele J (2017). Proposal for an index to evaluate dichotomous keys. Zookeys 685:83-89.
Crossref
|
|
|
|
|
Stagg BC, Donkin MC (2013). Teaching botanical identification to adults: Experience of the UK participatory science project open air laboratories. Journal of Biological Education 47(2):104-110.
Crossref
|
|
|
|
|
Strain SR, Chmielewski JG (2010). A simple computer application for the identification of Conifer Genera. The American Biology Teacher 72(5):301-304.
Crossref
|
|
|
|
|
Tofilski A (2018). DKey software for editing and browsing dichotomous keys. Zookeys 735:131-140.
Crossref
|
|
|
|
|
Upton R, Romm A (2010). Guidelines for herbal medicine use In: Botanical medicine for women's health, Romm A, Hardy ML, Mills S (eds.), Churchill Livingstone pp. 75-96.
Crossref
|
|
|
|
|
Walter DE, Winterton S (2007). Keys and the crisis in taxonomy: extinction or reinvention?. Annual review of Entomology 53:192-208.
Crossref
|
|
|
|
|
Yin S, Lin X, Liu L, Wei S (2016). Exploiting parallelism of imperfect nested loops on Course-Grained Reconfigurable Architectures. IEEE Transactions on Parallel and Distributed Systems 27:3199-3213.
Crossref
|
|